CloudSafetyNet: End-to-End Cloud Security
Security considerations are a major issue holding back the widespread adoption of cloud computing: many organisations are concerned about the confidentiality and integrity of their users' data when hosted in third-party public clouds. Today's cloud providers struggle to give strong security guarantees that user data belonging to cloud tenants will be protected "end-to-end", i.e. across the entire workflow of a complex cloud-hosted distributed application. The focus of the CloudSafetNet project is to fundamentally rethink how platform-as-a-service (PaaS) clouds should handle security requirements of applications. The overall goal is to provide the CloudSafetyNet middleware, a novel PaaS platform that acts as a "safety net", protecting against security violations caused by implementation flaws in applications ("intra-tenant security") or vulnerabilities in the cloud platform itself ("inter-tenant security").
CloudSafetyNet follows a "data-centric" security model: the integrity and confidentiality of application data is protected according to data flow policies -- agreements between cloud tenants and the provider specifying the permitted and prohibited exchanges of data between application components. It will enforce data flow policies through multiple levels of security mechanisms following a "defence-in-depth" strategy: based on policies, it creates "data compartments" that contain one or more components and isolate user data. A small privileged kernel, which is part of the middleware and constitutes a trusted computing base (TCB), tracks the flow of data between compartments and prevents flows that would violate policies. Previously such information flow control (IFC) models have been used successfully to enhance programming language, operating system and web application security.
Lightweight Monitoring to Detect Data Leakage in Clouds
When tenants deploy applications under the control of third-party cloud providers, they must trust the provider’s security mechanisms for inter-tenant isolation, resource sharing and access control. Despite a provider’s best efforts, accidental data leakage may occur due to misconfigurations or bugs in the cloud platform. Especially in Platform-as-a-Service (PaaS) clouds, which rely on weaker forms of isolation, the potential for unnoticed data leakage is high. Prior work to raise tenants’ trust in clouds relies on attestation, which limits the management flexibility of providers, or fine-grained data tracking, which has high overheads.
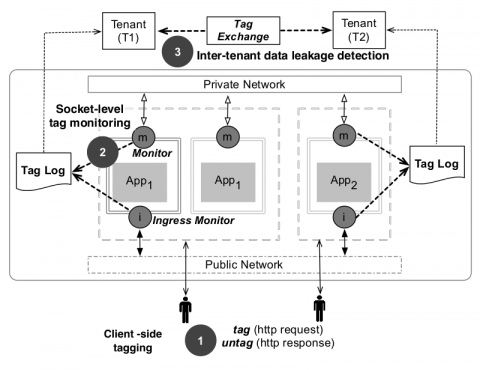
We propose a lightweight monitoring framework called CloudSafetyNet (CSN) that gives tenants visibility into the propagation of their application data in a cloud environment with low performance overhead. It exploits the incentive of tenants to co-operate with each other to detect accidental data leakage. There are three main steps in our approach:
- Using a client-side JavaScript library, CSN transparently adds opaque security tags to a subset of form fields in HTTP requests.
- Socket-level monitors maintain a log of observed tags flowing between application components. Monitors that sit at the entrypoint of client requests from the public network, called ingress monitors, help tenants to distinguish data was intended for their application from data that leaked from another application.
- Tenants retrieve their logs and identify foreign tags that indicate data leakage. To check the correct operation of CSN, tenants send probe requests with known tags and verify their logging.
Using an implementation of CSN deployed on the OpenShift and AppScale PaaS platforms, we show that it can discover misconfigurations and bugs with a negligible performance impact.
